Construction was among the top five business sectors targeted by cyberattacks in the second quarter of 2018, according to the latest “threat report” released earlier this month by eSentire, the largest pure-play managed detection and response service provider.
Based on intelligence gathered from more than 2,000 proprietary network and host-based detection sensors distributed globally in multiple industries, eSentire estimates that the number of attacks on Microsoft Internet Information Services (IIS) jumped to 1.7 million in the second quarter, from 2,000 in the first quarter. Most sources targeting IIS web servers originated from China-based IP addresses: according to Shodan, the global search engine for Internet-connected devices, there are 3.5 million IIS web servers exposed (with 1 million in China). The compromised servers largely originated from the Tencent and Alibaba sites.
eSentire observed IIS and WebLogic attacks originating from servers hosting Apache, RDP, SQL, IIS, and HTTP API services. Most of the records included known potential vulnerabilities based on server software version. Vulnerability records for attacking servers showed a steady increase. The majority of this growth appeared to come from Apache HTTP Servers, version 2.4.23. In the same period, records reporting vulnerabilities in IIS 7.5 and HTTP Server 2.4.10 appeared to diminish.
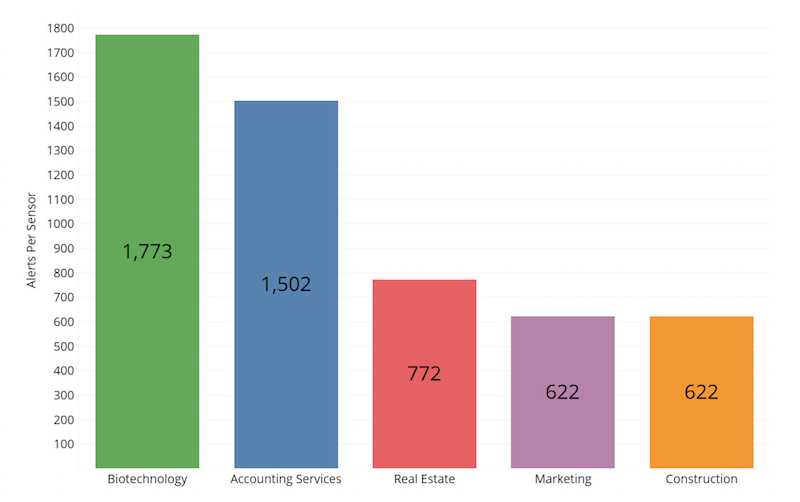
Four million potentially hostile events resulted in 57,000 alerts having been sent from eSentire’s SOC (Security Operations Center) between April 1 and June 30, 2018. Normalizing by sensor count, the top five affected industries were Biotechnology, Accounting Services, Real Estate, Marketing, and Construction. Regardless of industry, most attackers are probably looking to drive ad revenue or adopt compromised servers into their attack infrastructure, the report suggests.
The reason attacks continue, posits the report, is because most organizations have internal systems they hesitate to update for fear it will change or break something. These systems are sometimes accidentally exposed to background internet radiation which includes a firehose of exploits. Or, they are unaware that a patch is necessary or underestimate the gravity of failing to patch. This is an easily rectifiable problem that nevertheless lingers for many businesses.
There also was an increase, in general, in phishing attacks that used shipping invoice lures, despite an overall decline in the use of DocuSign—which facilities the exchanges of contracts and signed documents—as lures. Construction, Education, and Marketing experienced the largest amount of confirmed phishing attacks, with DocuSign dominating the lures observed; likely, these industries make frequent use of DocuSign in handling digital invoices and quotes due to remotely based business relationships and employees.
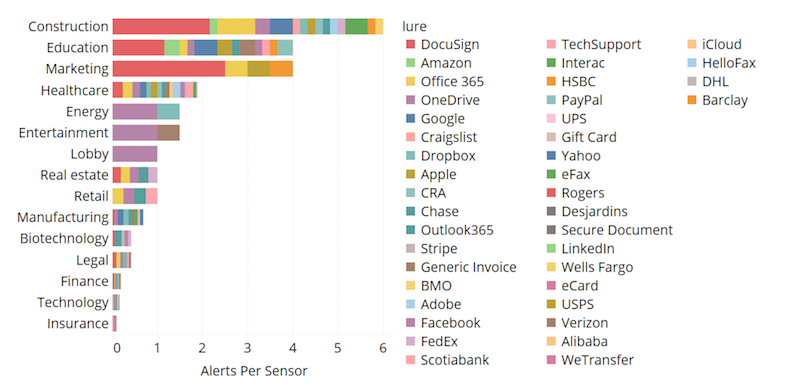
Construction was vulnerable to phishing attacks that used DocuSign as their primary lure. Image: eSentire
Real Estate experienced high volumes of D-Link home router exploit attempts. Marketing was subjected to a high volume of D-Link exploit attempts and a sizable degree of malicious PowerShell activity. And Construction experienced a large amount of Drupalgeddon2 attacks (the name given to an extremely critical vulnerability Drupal maintainers patched in late March).
PowerShell is a task-based command-line shell and scripting language built on .NET. PowerShell helps system administrators, and power-users can rapidly automate tasks that manage operating systems (Linux, macOS, and Windows) and processes. PowerShell commands let you manage computers from the command line.
In Q2 2018, the eSentire detection surface revealed that an obfuscated PowerShell realized an increase of 50% in commands, partly due to Emotet, a sophisticated malware.
Emotet, a four-year-old banking trojan, continues to evolve and emerge; antivirus solutions detected it, on average, only 22% of the time in the quarter. Emotet remains a popular choice for threat actors and was the most frequently observed malware due to numerous version updates and feature additions since it was first reported in 2014. Obfuscated malicious PowerShell commands increased 50% in Q2 2018.
Nearly half (49%) of Emotet samples included “invoice,” “payment,” or “account” in their file names. For Emotet’s competitor, Hancitor, fax documents were a popular lure (25%).
To protect against Emotet and to mitigate worming capabilities, Server Message Block Protocol (SMB) communications between systems in a network should be restricted via group policy settings or in the configuration of host-based Intrusion Prevention Systems (HIPS).
Malware, which is intended to damage or disable computers and systems, breaks down into four threat levels: malicious, suspicious, benign, and ambiguous (like false positives). Construction ranked fourth—behind Healthcare, Real Estate, and Marketing—for malware events (20 per sensor), and ranked second (after Accounting Services) for reputational blocks (about 5.25 alerts per sensor), which occur when known bad Internet Protocols (IPs) are detected trying to establish connections with monitored clients. Accounting Services and Construction are known to have large threat surfaces.
Some IPs only attempted an IIS or WebLogic exploit, while other IPs attempted both. The IPs attempting IIS and WebLogic persisted throughout the quarter, said eSentire, but those tended to rise with the emergence of other potential campaigns, indicating some threat actors may have an array of botnets in different configurations.
Related Stories
| Aug 11, 2010
Great Solutions: Business Management
22. Commercial Properties Repositioned for University USE Tocci Building Companies is finding success in repositioning commercial properties for university use, and it expects the trend to continue. The firm's Capital Cove project in Providence, R.I., for instance, was originally designed by Elkus Manfredi (with design continued by HDS Architects) to be a mixed-use complex with private, market-...
| Aug 11, 2010
Seven tips for specifying and designing with insulated metal wall panels
Insulated metal panels, or IMPs, have been a popular exterior wall cladding choice for more than 30 years. These sandwich panels are composed of liquid insulating foam, such as polyurethane, injected between two aluminum or steel metal face panels to form a solid, monolithic unit. The result is a lightweight, highly insulated (R-14 to R-30, depending on the thickness of the panel) exterior clad...
| Aug 11, 2010
Nurturing the Community
The best seat in the house at the new Seahawks Stadium in Seattle isn't on the 50-yard line. It's in the southeast corner, at the very top of the upper bowl. "From there you have a corner-to-corner view of the field and an inspiring grasp of the surrounding city," says Kelly Kerns, project leader with architect/engineer Ellerbe Becket, Kansas City, Mo.
| Aug 11, 2010
AIA Course: Historic Masonry — Restoration and Renovation
Historic restoration and preservation efforts are accelerating throughout the U.S., thanks in part to available tax credits, awards programs, and green building trends. While these projects entail many different building components and systems, façade restoration—as the public face of these older structures—is a key focus. Earn 1.0 AIA learning unit by taking this free course from Building Design+Construction.
| Aug 11, 2010
AIA Course: Enclosure strategies for better buildings
Sustainability and energy efficiency depend not only on the overall design but also on the building's enclosure system. Whether it's via better air-infiltration control, thermal insulation, and moisture control, or more advanced strategies such as active façades with automated shading and venting or novel enclosure types such as double walls, Building Teams are delivering more efficient, better performing, and healthier building enclosures.
| Aug 11, 2010
Glass Wall Systems Open Up Closed Spaces
Sectioning off large open spaces without making everything feel closed off was the challenge faced by two very different projects—one an upscale food market in Napa Valley, the other a corporate office in Southern California. Movable glass wall systems proved to be the solution in both projects.
| Aug 11, 2010
AIA course: MEP Technologies For Eco-Effective Buildings
Sustainable building trends are gaining steam, even in the current economic downturn. More than five billion square feet of commercial space has either been certified by the U.S. Green Building Council under its Leadership in Energy and Environmental Design program or is registered with LEED. It is projected that the green building market's dollar value could more than double by 2013, to as muc...
| Aug 11, 2010
Thrown For a Loop in China
While the Bird's Nest and Water Cube captured all the TV coverage during the Beijing Olympics in August, the Rem Koolhaas-designed CCTV Headquarters in Beijing—known as the “Drunken Towers” or “Big Shorts,” for its unusual shape—is certain to steal the show when it opens next year.
| Aug 11, 2010
World's tallest all-wood residential structure opens in London
At nine stories, the Stadthaus apartment complex in East London is the world’s tallest residential structure constructed entirely in timber and one of the tallest all-wood buildings on the planet. The tower’s structural system consists of cross-laminated timber (CLT) panels pieced together to form load-bearing walls and floors. Even the elevator and stair shafts are constructed of prefabricated CLT.
| Aug 11, 2010
Integrated Project Delivery builds a brave, new BIM world
Three-dimensional information, such as that provided by building information modeling, allows all members of the Building Team to visualize the many components of a project and how they work together. BIM and other 3D tools convey the idea and intent of the designer to the entire Building Team and lay the groundwork for integrated project delivery.